Tag: technical
-

Baiting MEV Bots: UniV2 Token Trapper
So many MEV bots take money from people but why don't people take money from them? I always thought about this when I was in my web3 cybersec assembly arc. I got quite fascinated with reverse engineering them and the contracts they interected with and realised there are some interesting things you can do with the uniswap code, since it has a few assumptions with the tokens you provide to create the pairs. Although not very practical it's definitely an intereting thought experiment that can provoke some further creativity!
#technical
#mev
-

Entering The Dark MEV Forest
Gain insight into the difficult field of earn about how to research about Ethereum MEV bots on-chain so you gain the knowledge and skills to start building your own and dominate the MEV market! With hundreds of thousands of dollars lying in these smart contracts it's a perfect time to enter the dark MEV forest!
#technical
#mev
#web3
-

Generating Custom Assembly Smart Contracts
2 years ago I wrote a component that allowed me to generate any custom assembly smart contract on the fly to automatically create exploits without needing to do any manual work. I had a montiroing system that would provide the inputs and the bytecode generator would chug along and spit out an executable program that I could deploy and call on with a bundle of transactions. In this article I'll share the core of that codebase to get you up to speed! Buckle up, anon. There isn't any other article like this revealing these trade secrets!
#technical
#cybersecurity
#mev
#web3
-
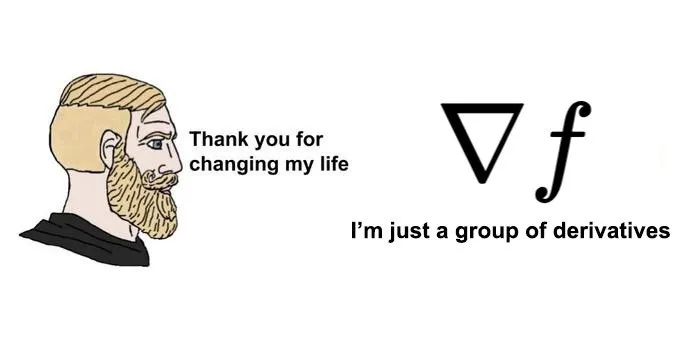
Understanding Gradient Descent
Machine Learning (ML) and Artificial Intelligence (AI) relies heavily on this very intuitive differentiation-based algorithm called gradient descent. It gets us closer to our desired minima or maxima by starting with a value and adjusting that value based on the change of our gradient. In this article you'll learn to understand what is gradient descent and all the component apart of it. And then explore a few modifications of it from simple to advanced to solidify your understanding!
#technical
#math
-

How To Build a MEV Bot
So, you've been doing too much PvE and want to get into the on-chain PvP scene. Be wary traveler, this is a lonely environment to be in if you're playing solo. You will spend months building to upkeep your infrastructure to stay competitive in the MEV world on Ethereum, unless you find a very niche strategy. However, the booty is high and mighty if you manage to pull it off! If that sounds like something you want to do, continue on.
#technical
#mev
#web3
-

A Low-Level Guide To Solidity's Storage Management
Learn how the EVMs storage system works by interacting with it through smart contracts using solidity's inline assembly/yul, taking you a step closer to bridging the gap between high and low level programming! We'll walkthrough each encounter you will face by learning deal with them using bitwise operations alongside SLOAD and SSTORE to control the EVMs storage at will.
#technical
#web3
#assembly
-

Memware: Generalised Frontrunners
If there was malware native to crypto, it would be generalised frontrunners (GFs). These pesky critters analyse each transaction that enters the mempool, and like sharks, detecting vulnerable pending transactions, striking when they observe a profitable transaction. In this article we'll unravel, step-by-step, how one of these sophiscated creatures work in hopes to shed light on the depths of the mempool.
#technical
#mev
#web3
-

Swimming Safely In The Public Mempool: MEV Smart Contract Obfuscation Techniques
In blockchain, generalized frontrunners in MEV abuse the well-known standards of smart contract, therefore obfuscation techniques are essential for MEV operators. Over the past year I've created some zero-day techniques for avoiding these sharks in the mempool of Ethereum and all other existing blockchains in web3. Whether you're a semi-vet like DeGatchi or are just starting in the the MEV world of ETH, you are able to deploy these obfuscation techniques on day 1 to potentially gain an edge on your competition. Godspeed, anon!
#technical
#mev
#cybersecurity
-
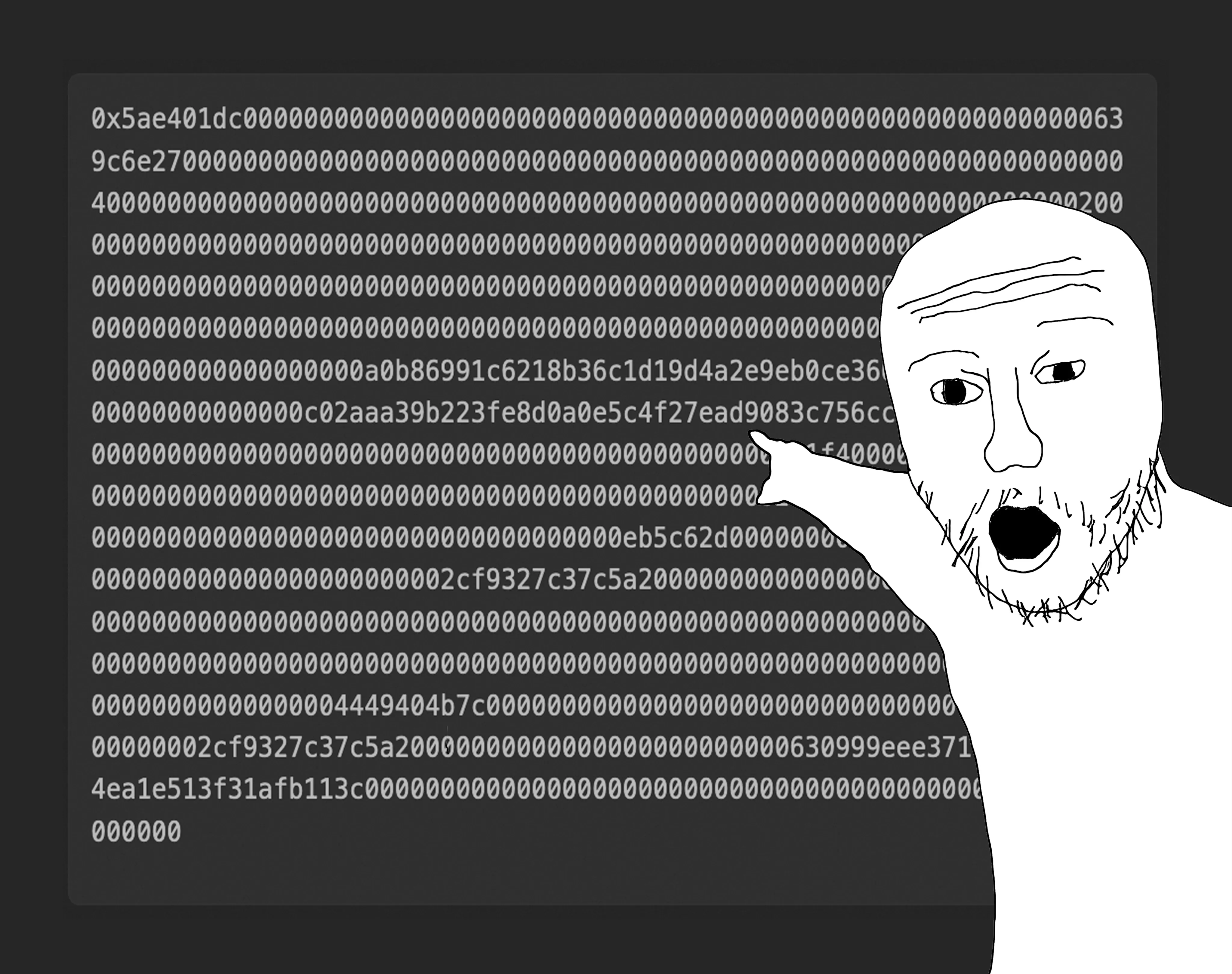
Reversing The EVM: Raw Calldata
You may have have wondered how to decipher and read evm calldata, then attempted to read the transaction calldata of an Ethereum smart contract, only to become confused at a certain point. The EVM (and other L1 forks) encode and decode calldata in a specific way for static and dynamic types, which can be initially confusing. In this article, we will delve into the encoding sequence of calldata so that you can comprehend any verified or unverified smart contract transactions and understand the bytes. By doing so, I hope to empower you to create your own raw calldata.
#technical
#cybersecurity
#assembly
#web3
-

Smart Contract Obfuscation Techniques
How do you prevent MEV frontrunners from stealing your transactions, copying your smart contracts and understanding your strategies built into your smart contracts on-chain? Let me take you into the depths of the dark forest, where bleeding-edge smart contract bytecode obfuscation techniques are developed to keep your secrets hidden for longer.
#technical
#cybersecurity
#assembly
#web3
